App Information of Magisk
| App Name | Magisk v20210116 |
|---|---|
| Genre | Zip file |
| Size | 2.5 MB |
| Latest Version | 20210116 |
| Get it On |  |
| Update | Jan 16, 2021 |
| Package Name | Magisk-uninstaller-20210116.zip |
| Rating | 4.8 ( 798 ) |
| Installs | 4756 |
Description of Magisk
Magisk uninstaller 20210116 zip download. This uninstaller file released in Magisk v21.3.
It adds a workaround for devices with buggy F2FS Linux kernel drivers.
tools.md
Magisk Tools
Magisk comes with a huge collections of tools for installation, daemons, and utilities for developers. This documentation covers the 3 binaries and all included applets. The binaries and applets are shown below:
magiskboot /* binary */magiskinit /* binary */magiskpolicy -> magiskinitsupolicy -> magiskinitmagisk /* binary */magiskhide -> magiskresetprop -> magisksu -> magiskNote: The Magisk zip you download only contains `magiskboot`, `magiskinit`, and `magiskinit64`. The binary `magisk` is compressed and embedded into `magiskinit(64)`. Push `magiskinit(64)` to your device and run `./magiskinit(64) -x magisk <path>` to extract `magisk` out of the binary.
magiskboot
A tool to unpack / repack boot images, parse / patch / extract cpio, patch dtb, hex patch binaries, and compress / decompress files with multiple algorithms.
`magiskboot` natively supports (which means it does not rely on external tools) common compression formats including `gzip`, `lz4`, `lz4_legacy` ([only used on LG](https://events.static.linuxfound.org/sites/events/files/lcjpcojp13_klee.pdf)), `lzma`, `xz`, and `bzip2`.
The concept of `magiskboot` is to make boot image modification simpler. For unpacking, it parses the header and extracts all sections in the image, decompressing on-the-fly if compression is detected in any sections. For repacking, the original boot image is required so the original headers can be used, changing only the necessary entries such as section sizes and checksum. All sections will be compressed back to the original format if required. The tool also supports many CPIO and DTB operations.
Usage: magiskboot <action> [args…]
Supported actions:
unpack [-n] [-h] <bootimg>
Unpack <bootimg> to, if available, kernel, kernel_dtb, ramdisk.cpio,
second, dtb, extra, and recovery_dtbo into current directory.
If ‘-n’ is provided, it will not attempt to decompress kernel or
ramdisk.cpio from their original formats.
If ‘-h’ is provided, it will dump header info to ‘header’,
which will be parsed when repacking.
Return values:
0:valid 1:error 2:chromeosrepack [-n] <origbootimg> [outbootimg]
Repack boot image components from current directory
to [outbootimg], or new-boot.img if not specified.
If ‘-n’ is provided, it will not attempt to recompress ramdisk.cpio,
otherwise it will compress ramdisk.cpio and kernel with the same method
in <origbootimg> if the file provided is not already compressed.hexpatch <file> <hexpattern1> <hexpattern2>
Search <hexpattern1> in <file>, and replace with <hexpattern2>cpio <incpio> [commands…]
Do cpio commands to <incpio> (modifications are done in-place)
Each command is a single argument, add quotes for each command
Supported commands:
exists ENTRY
Return 0 if ENTRY exists, else return 1
rm [-r] ENTRY
Remove ENTRY, specify [-r] to remove recursively
mkdir MODE ENTRY
Create directory ENTRY in permissions MODE
ln TARGET ENTRY
Create a symlink to TARGET with the name ENTRY
mv SOURCE DEST
Move SOURCE to DEST
add MODE ENTRY INFILE
Add INFILE as ENTRY in permissions MODE; replaces ENTRY if exists
extract [ENTRY OUT]
Extract ENTRY to OUT, or extract all entries to current directory
test
Test the current cpio’s patch status
Return values:
0:stock 1:Magisk 2:unsupported (phh, SuperSU, Xposed)
patch
Apply ramdisk patches
Configure with env variables: KEEPVERITY KEEPFORCEENCRYPT
backup ORIG
Create ramdisk backups from ORIG
restore
Restore ramdisk from ramdisk backup stored within incpio
sha1
Print stock boot SHA1 if previously backed up in ramdiskdtb <input> <action> [args…]
Do dtb related actions to <input>
Supported actions:
print [-f]
Print all contents of dtb for debugging
Specify [-f] to only print fstab nodes
patch
Search for fstab and remove verity/avb
Modifications are done directly to the file in-place
Configure with env variables: KEEPVERITYsplit <input>
Split image.*-dtb into kernel + kernel_dtbsha1 <file>
Print the SHA1 checksum for <file>cleanup
Cleanup the current working directorycompress[=method] <infile> [outfile]
Compress <infile> with [method] (default: gzip), optionally to [outfile]
<infile>/[outfile] can be ‘-‘ to be STDIN/STDOUT
Supported methods: bzip2 gzip lz4 lz4_legacy lz4_lg lzma xzdecompress <infile> [outfile]
Detect method and decompress <infile>, optionally to [outfile]
<infile>/[outfile] can be ‘-‘ to be STDIN/STDOUT
Supported methods: bzip2 gzip lz4 lz4_legacy lz4_lg lzma xz
“`magiskinit
This binary will replace `init` in the ramdisk of a Magisk patched boot image. It is originally created for supporting devices using system-as-root, but the tool is extended to support all devices and became a crucial part of Magisk. More details can be found in the **Pre-Init** section in [Magisk Booting Process](details.md#magisk-booting-process).
magiskpolicy
(This tool is aliased to `supolicy` for compatibility with SuperSU’s sepolicy tool)
An applet of `magiskinit`. This tool could be used for advanced developers to modify SELinux policies. In common scenarios like Linux server admins, they would directly modify the SELinux policy sources (`*.te`) and recompile the `sepolicy` binary, but here on Android we directly patch the binary file (or runtime policies).
All processes spawned from the Magisk daemon, including root shells and all its forks, are running in the context `u:r:magisk:s0`. The rule used on all Magisk installed systems can be viewed as stock `sepolicy` with these patches: `magiskpolicy –magisk ‘allow magisk * * *’`.
“`
Usage: magiskpolicy [–options…] [policy statements…]Options:
–help show help message for policy statements
–load FILE load policies from FILE
–load-split load from precompiled sepolicy or compile
split policies
–compile-split compile split cil policies
–save FILE save policies to FILE
–live directly apply sepolicy live
–magisk inject built-in rules for a minimal
Magisk selinux environment
–apply FILE apply rules from FILE, read and parsed
line by line as policy statementsIf neither –load or –compile-split is specified, it will load
from current live policies (/sys/fs/selinux/policy)One policy statement should be treated as one parameter;
this means each policy statement should be enclosed in quotes.
Multiple policy statements can be provided in a single command.Statements has a format of “<rule_name> [args…]”.
Arguments labeled with (^) can accept one or more entries. Multiple
entries consist of a space separated list enclosed in braces ({}).
Arguments labeled with (*) are the same as (^), but additionally
support the match-all operator (*).Example: “allow { s1 s2 } { t1 t2 } class *”
Will be expanded to:allow s1 t1 class { all-permissions-of-class }
allow s1 t2 class { all-permissions-of-class }
allow s2 t1 class { all-permissions-of-class }
allow s2 t2 class { all-permissions-of-class }Supported policy statements:
“allow *source_type *target_type *class *perm_set”
“deny *source_type *target_type *class *perm_set”
“auditallow *source_type *target_type *class *perm_set”
“dontaudit *source_type *target_type *class *perm_set”“allowxperm *source_type *target_type *class operation xperm_set”
“auditallowxperm *source_type *target_type *class operation xperm_set”
“dontauditxperm *source_type *target_type *class operation xperm_set”
– The only supported operation is ‘ioctl’
– xperm_set format is either ‘low-high’, ‘value’, or ‘*’.
‘*’ will be treated as ‘0x0000-0xFFFF’.
All values should be written in hexadecimal.“permissive ^type”
“enforce ^type”“typeattribute ^type ^attribute”
“type type_name ^(attribute)”
– Argument ‘attribute’ is optional, default to ‘domain’“attribute attribute_name”
“type_transition source_type target_type class default_type (object_name)”
– Argument ‘object_name’ is optional“type_change source_type target_type class default_type”
“type_member source_type target_type class default_type”“genfscon fs_name partial_path fs_context”
“`magisk
When the magisk binary is called with the name `magisk`, it works as a utility tool with many helper functions and the entry points for several Magisk services.
“`
Usage: magisk [applet [arguments]…]
or: magisk [options]…Options:
-c print current binary version
-v print running daemon version
-V print running daemon version code
–list list all available applets
–remove-modules remove all modules and reboot
–install-module ZIP install a module zip fileAdvanced Options (Internal APIs):
–daemon manually start magisk daemon
–[init trigger] start service for init trigger
Supported init triggers:
post-fs-data, service, boot-complete
–unlock-blocks set BLKROSET flag to OFF for all block devices
–restorecon restore selinux context on Magisk files
–clone-attr SRC DEST clone permission, owner, and selinux context
–clone SRC DEST clone SRC to DEST
–sqlite SQL exec SQL commands to Magisk database
–path print Magisk tmpfs mount pathAvailable applets:
su, resetprop, magiskhide
“`su
An applet of `magisk`, the MagiskSU entry point. Good old `su` command.
Usage: su [options] [-] [user [argument…]]
Options:
-c, –command COMMAND pass COMMAND to the invoked shell
-h, –help display this help message and exit
-, -l, –login pretend the shell to be a login shell
-m, -p,
–preserve-environment preserve the entire environment
-s, –shell SHELL use SHELL instead of the default /system/bin/sh
-v, –version display version number and exit
-V display version code and exit
-mm, -M,
–mount-master force run in the global mount namespaceNote: even though the `-Z, –context` option is not listed above, the option still exists for CLI compatibility with apps designed for SuperSU. However the option is silently ignored since it’s no longer relevant.
resetprop
An applet of `magisk`. An advanced system property manipulation utility. Check the [Resetprop Details](details.md#resetprop) for more background information.
Usage: resetprop [flags] [options…]
Options:
-h, –help show this message
(no arguments) print all properties
NAME get property
NAME VALUE set property entry NAME with VALUE
–file FILE load props from FILE
–delete NAME delete propertyFlags:
-v print verbose output to stderr
-n set props without going through property_service
(this flag only affects setprop)
-p read/write props from/to persistent storage
(this flag only affects getprop and delprop)magiskhide
An applet of `magisk`, the CLI to control MagiskHide. Use this tool to communicate with the daemon to change MagiskHide settings.
Usage: magiskhide [action [arguments…] ]
Actions:
status Return the status of magiskhide
enable Start magiskhide
disable Stop magiskhide
add PKG [PROC] Add a new target to the hide list
rm PKG [PROC] Remove target(s) from the hide list
ls Print the current hide list
exec CMDs… Execute commands in isolated mount
namespace and do all hide unmounts
Content
- What is Android Rooting?
- What Magisk Manager?
- History of magisk manager apk
- Why you should do a Magisk download?
- How to Download Magisk Latest Version For Android 2021
- Magisk Manager installation on Android - External method
- Magisk Manager installation on Android - Custom Recovery option
- Uninstalling Magisk manager apk download
- FAQs
- Is rooting the android devices legal?
- Is Magisk Manager Risk-Free?
- Can Magisk Manager download for free?
- Does Magisk compatible with my android version?
- Why is Magisk won't function well on my phone?
What is Android Rooting?
It simply means unlocking the android operating system to grant access to the unauthorized section of the phone. Even though you own the handset, you don't have full authority over the phone. You just log in to the system as a user. But after you root it, you can do whatever you want with your device. Such as installing apps that unapproved, unlock the bootloader and remove unwanted bloatware, installing custom ROMs, and customize it furthermore as you wish.
It's kind of similar to apple jailbreak. And the most amazing part is android rooting can also be led to high performance and longer battery life. Well, now you know about rooting. Then what is the connection between android rooting and the Magisk Manager? Hang on, we are going to talk about it.
What Magisk Manager?
As they say it, it's a mask for android. Does that complicate things for you even more? well, if you are new to android rooting you probably have no idea that there are some struggles that have to be overcome when you have a rooted device. If you have a rooted android phone, you don't get OTA updates! Yeah, that's right. You have to unroot it, then get the update and root again. And some applications won't even allow running in rooted handsets. Especially banking applications.
That's when the Magisk manager apk comes to the rescue. It's a systemless rooting solution. It can cover the rooted system like a mask and you won't have to be bothered to go between rooting and unrooting. It doesn't affect the core code either. You can get OTA updates, use banking applications and do whatever you couldn't do from a rooted mobile phone.
History of magisk manager apk
Topjohnwu was a developer in the android developer team. He was the one who launched the Magisk Manager in 2016 as the best solution that can go through the android safety net. And since the first release to the latest Magisk apk version 23.0, he has been developing it adding convenient features, and upgrading it. So now we can go for Magisk manager apk download which has much more convenient characteristics than then.
Why you should do a Magisk download?
There are a bunch of new characteristics that come with Magisk latest version 23.0.0. According to the Magisk manager GitHub page, we can expect more in the future because the developer planning to add more improvements in the future as well.
- Magisk Manager apk can download to any regular android phone and then you can root it.
- It allows you to go through google safety net.
- It let you add and modify files. Furthermore, since it is open source you can make changes to default coding and make it work for you as you want.
- The mount feature is really convenient. It allows you to change the core and partition levels as well. Moreover, you can make changes to all the system and media files and store them as you prefer in memory.
- Read-only files including prop files can be changed from the Resetprop feature.
- You can build and include your own repositories in the application.
- You can download any app from any site without the approval of the android OS.
How to Download Magisk Latest Version For Android 2021
Now the design and implementation are much convenient in Magisk than earlier you don't have to download separate files for Magisk zip and Magisk manager apk. There is only one app now.
But before you do the Magisk manager apk download there are some things that you should take care of.
- It's convenient to learn some of the basics in ADB and fastboot.
- The device bootloader should be unlocked before installing the Magisk zip.
- You have to flash custom ROM once again to use stock boot.img. But only if you are using the boot.img mods.
- Custom kernel installation is necessary.
Magisk Manager installation on Android - External method
1. First go Magisk manager apk download for the mobile phone.
2. Enable the unknown sources to turn on un settings and then install the downloaded Magisk app
3. Now install it once more by clicking on the "install" button on the message you will see.
4. Actually that's all. Now you have installed it.
Magisk Manager installation on Android - Custom Recovery option
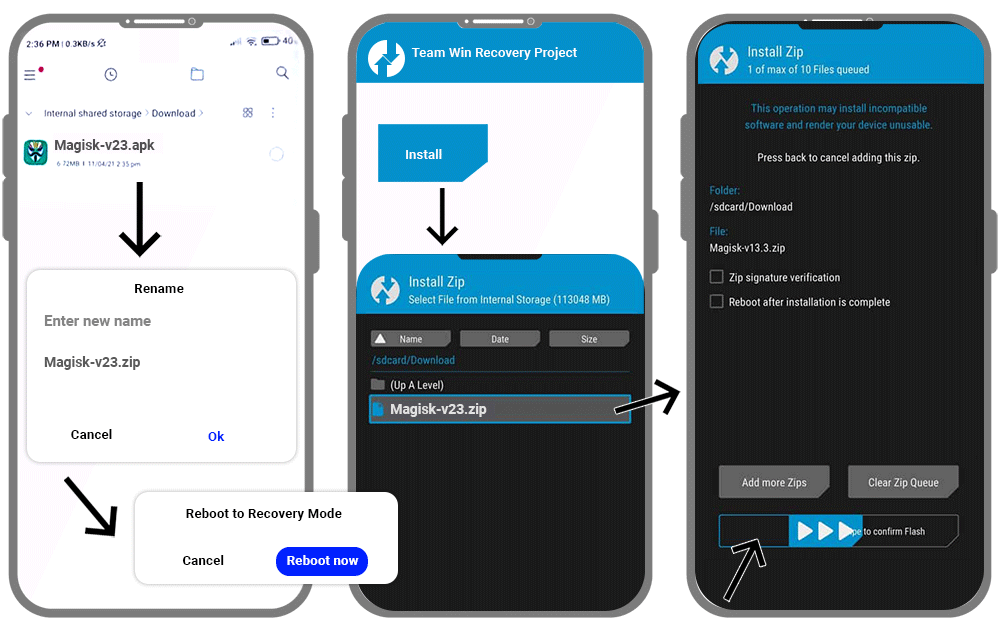
TWRP is a custom recovery solution for Android mobile phones. After you install this tool, you can back up the system and download thrid party firmware as well. Therefore make sure to back the system before starting to proceed.
- First, install TWRP on your android phone.
- Then you have to download Magisk Manager APK
- Now you have to rename the extension to .apk for the .zip. (Magisk zip)
- Reboot your device into TWRP recovery mode.
- Now click the install button on the TWRP recovery boot menu
- Then go to internal storage -->Magisk.zip --> Select storage
- Next, install the zip file
- When it completes the installation open the file -->Reboot system
- If it works you have installed Magisk Manager successfully.
Uninstalling Magisk manager apk download
Method 1 - Using the App
- Magisk app icon -->Uninstall --> An alert message --> Complete Uninstall
- Next, the app asks for permission to activate the uninstaller file. -->Click allow
- Then the Magisk uninstaller will be downloaded and uninstall the installed Magisk APK.
- Finally, it will be reboot automatically.
Method 2 - Using TWRP Recovery
- First, you should have the Magisk app on your phone.
- Next, rename its extension to uninstall.zip.
- Then switch off the mobile phone and boot it into the recovery mode.
- Now click the install button on the recovery menu and select the Magisk Uninstaller zip file.
- Slide the slider then and the installation will be started.
- Finally, reboot the device and Magisk will be removed once you check it.
FAQs
Is rooting the android devices legal?
In short, Yes. But it is legal as long as you root your android smartphone. Because many manufacturers allow it nowadays. However, rooting android tablets are illegal.
Is Magisk Manager Risk-Free?
Since there are many users but never get complaints about malware, viruses, or any spam, we can assure you Magisk is a pretty good and safe rooting solution. Furthermore, it won't modify boot partitions or the system partitions. And neither install third-party applications without your consent.
Can Magisk Manager download for free?
Absolutely. It offers the facilities to download, install and manage the device completely free of charge.
Does Magisk compatible with my android version?
It's compatible with all the android versions above 4.1 and 4.2 And your compressed boot image on an android mobile phone should be gzip compressed boot.img.
Why is Magisk won't function well on my phone?
If you have installed the application externally, that might be the reason for this issue. Therefore it's better if you uninstall that and install Magisk apk to your device's internal storage.